






















Your impenetrable shield against modern threats. Stop sophisticated attacks targeting hardware or software with advanced security policies and real-time monitoring.
Fortress around your data. DLP goes beyond content inspection, analyzing context across applications and networks to proactively prevent sensitive information leaks.
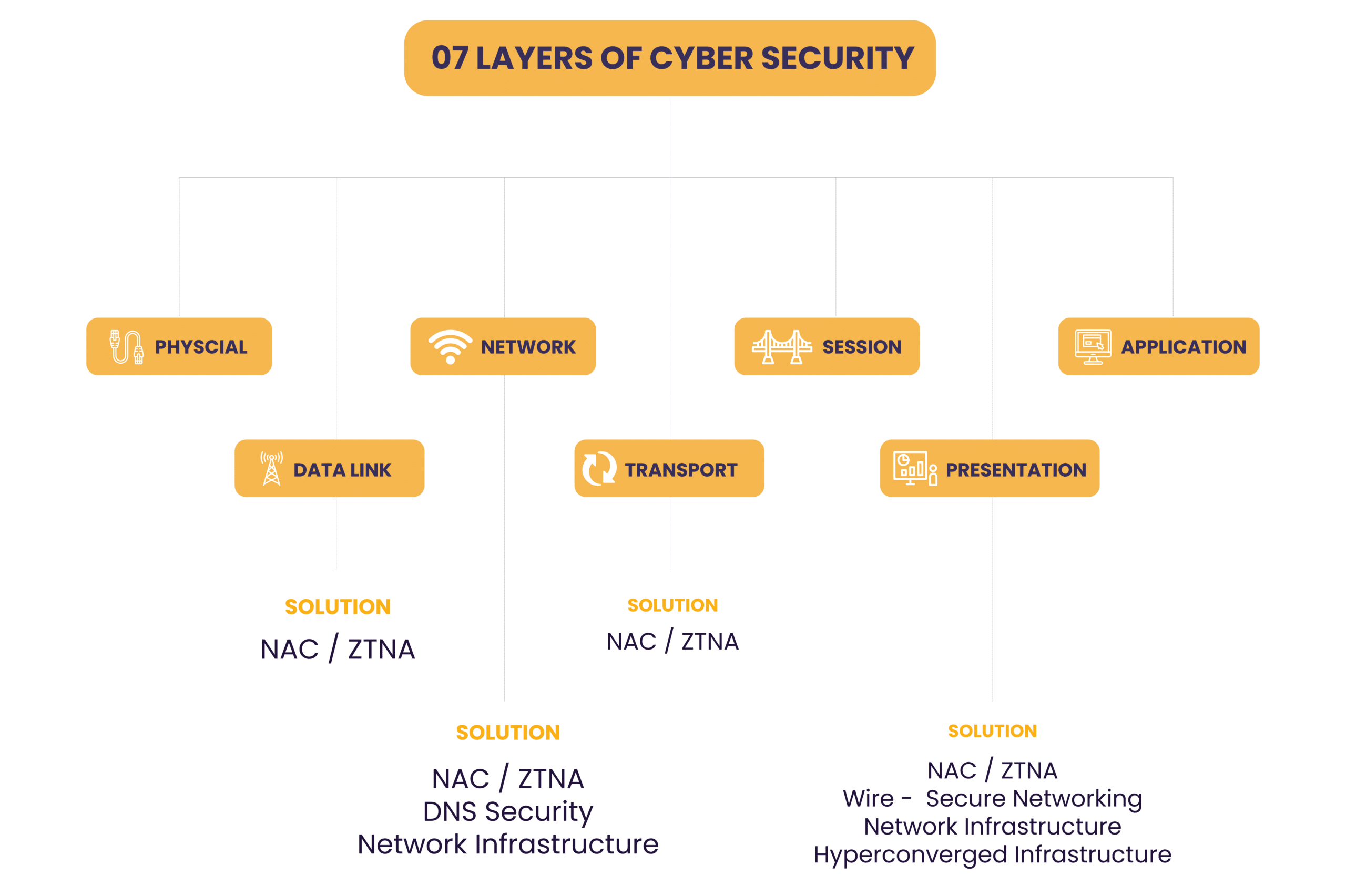
No safe haven for infected devices. NAC quarantines them, while ZTNA grants access only to verified users and devices, eliminating trust-based vulnerabilities.
Your cloud guardian angel. CASB sits between you and the cloud, enforcing your security policies and ensuring your data remains protected even in the cloud.
Untrusted code? No problem. Our sandbox safely inspects and tests suspicious code, guaranteeing the quality and reliability of your applications.
Domain defense system. DNS Security safeguards your domain name system with digital signatures, blocking attacks and ensuring data validity.
Add an extra layer of protection. MFA requires multiple credentials for login, making it significantly harder for attackers to breach your systems.
Your data defense squad. CTP combines the power of machine learning and human expertise to continuously protect your content and data from ever-evolving threats.
Guarding your web presence. WAF shields your web servers, applications, and services from malicious attacks launched over the internet.
Keep your wireless network impenetrable. Our secure solutions prevent unauthorized access and protect your systems from wireless threats.
Endpoint protection with superpowers. Our solutions secure your remote devices, providing extended detection and response, real-time threat hunting, and proactive vulnerability management.
Fortified foundation. We implement best practices and security tools to safeguard your network, ensuring seamless and secure communication between connected devices.
Stop malicious emails in their tracks. Our advanced email security solutions prevent attacks, protect against non-compliance, and keep your inboxes safe.
Secure simplicity. Hyperconverged infrastructure combines security with scalability, offering simplified management and robust protection for your entire system.
Real-time insights, actionable intelligence. SIEM analyzes security alerts from your network and applications, providing comprehensive monitoring and forensic reports for informed decision-making.
Expose and eliminate vulnerabilities before attackers do. VAPT identifies security weaknesses and simulates real-world attacks, enabling proactive remediation and enhanced security posture.
Secure code, secure applications. These testing tools uncover vulnerabilities in your applications, helping you build secure and reliable software.
Go beyond endpoint security. IAM safeguards all identities within your company, preventing unauthorized access and identity-driven breaches.
Secure your industrial operations. We provide specialized solutions to protect your operational technology (OT) systems from cyber threats.
Secure your connected devices. Our IoT security solutions safeguard your internet-of-things devices, ensuring their secure operation and data protection.
Empower your employees to be your security champions. We offer comprehensive security awareness training programs to educate your staff and minimize human error risk.
Get an independent evaluation of your security posture. Our experienced professionals are ISO:27001 certified and they conduct thorough assessments and audits, providing actionable recommendations for improvement.
Understand your overall security landscape. We provide a comprehensive assessment of your cybersecurity posture, identifying strengths, weaknesses, and areas for improvement.
Ambsan, Pakistan Plot 152/F, P.E.C.H.S Block # 2, Khalid Bin Walid Road, Karachi
